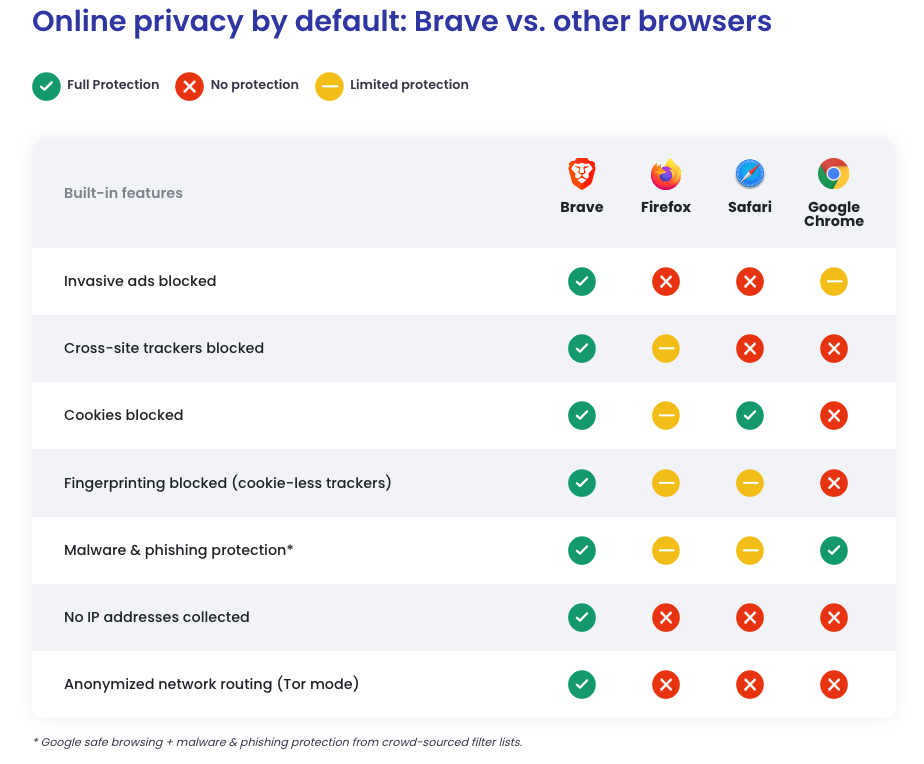
Introduction to Browser Security
Web browsers have become an essential tool in our daily lives, serving as gateways to the vast realm of the internet. However, this convenience also exposes us to various security threats that can compromise our sensitive information and privacy. Browser security encompasses a set of measures implemented to protect users from these threats, ensuring a safe and secure online experience.
Definition and Importance of Browser Security
Browser security refers to the collective efforts undertaken by browser developers, security researchers, and users themselves to safeguard against malicious activities that target web browsers. It involves implementing robust security features within browsers and adhering to best practices that mitigate risks associated with browsing.
The importance of browser security cannot be overstated when considering the vast amount of personal and financial data transmitted through browsers on a daily basis. Protecting sensitive information like login credentials, credit card details, or personal identities has become paramount in an era where cybercriminals continually exploit vulnerabilities within browsers.
Brief History of Browser Vulnerabilities and Attacks
Over the years, web browsers have been plagued by numerous vulnerabilities that have led to devastating attacks on individuals, businesses, and even governments. The earliest vulnerabilities were often related to flaws in handling HTML tags or executing JavaScript code securely. These loopholes allowed attackers to inject malicious scripts or redirect users towards fraudulent websites aimed at stealing their confidential data.
One infamous example is the rise of phishing attacks in the early 2000s when cybercriminals began impersonating legitimate websites through email campaigns. Users were tricked into divulging their login credentials or financial information on counterfeit web pages cleverly designed to look authentic.
Furthermore, an alarming number of browser-based exploits emerged during this period due to inadequate patching mechanisms and slower response times from vendors in addressing vulnerabilities promptly. As technology evolved and web applications became more complex, so did browser attacks become more sophisticated.
Cross-Site Scripting (XSS) attacks emerged as a major threat, enabling attackers to inject malicious scripts into trusted websites and hijack user sessions or steal sensitive data. The relatively recent rise of Man-in-the-Middle (MitM) attacks further raised concerns regarding browser security.
Cybercriminals leveraged vulnerabilities in the underlying encryption protocols utilized by browsers to intercept communication between users and websites, allowing them to eavesdrop on confidential information. As we delve deeper into this article, we will explore the current state of browser security, the common threats users face while browsing, and the preventive measures and best practices that can be adopted to ensure a secure online experience.
Understanding Web Browsers
Overview of Popular Web Browsers (Chrome, Firefox, Safari, Edge)
Web browsers have become an indispensable tool for online activities, and several popular options dominate the market. Chrome, developed by Google, is widely regarded as the most popular browser due to its speed and user-friendly interface.
Firefox, an open-source browser created by Mozilla Foundation, focuses on privacy and customization options. Safari, the default browser on Apple devices, is known for its sleek design and performance optimization for Apple’s ecosystem.
Microsoft Edge is a relatively new entrant that replaced Internet Explorer and showcases improved security features along with seamless integration between Windows devices. Each of these browsers inherently comes with unique attributes that cater to different user preferences.
Chrome excels in providing a vast array of extensions and plugins while prioritizing usability. Firefox shines in terms of privacy enhancements like enhanced tracking protection and comprehensive security settings customization.
Safari emphasizes optimization for Apple’s hardware ecosystem while ensuring strong privacy measures through intelligent tracking prevention technology. Microsoft Edge stands out with its built-in security features like SmartScreen phishing protection and robust sandboxing capabilities.
Comparison of Their Security Features and Updates
When it comes to browser security features, all popular web browsers continuously strive to enhance their defenses against emerging threats. Chrome’s sandboxing technology isolates each tab from others, making it difficult for malicious code to spread across multiple tabs or compromise the entire system. Additionally, regular updates from Google ensure timely fixes for vulnerabilities.

Firefox adopts a multi-layered approach to security by implementing various features such as sandboxing processes per tab along with strict content blocking policies that mitigate potential threats effectively. Frequent updates address any vulnerabilities discovered during continuous community testing.
Safari boasts strong anti-tracking measures that prevent advertisers from monitoring users’ browsing habits without consent or compromising their online privacy rights significantly. It also utilizes process isolation techniques similar to other browsers to enhance security.
Microsoft Edge focuses on robust security measures, including SmartScreen phishing protection, which warns users about potentially dangerous websites. It also benefits from Microsoft’s strong commitment to regular updates and integration with Windows Defender for added protection against malware.
While all popular web browsers prioritize security, Chrome stands out for its extensive plugin ecosystem and usability, Firefox emphasizes privacy and customization options, Safari offers optimized performance for Apple devices with a focus on privacy protections, and Microsoft Edge showcases strong security features integrated with Windows ecosystem. Ultimately, the choice of browser depends on one’s specific requirements and priorities regarding features, performance, and security.
Common Browser Security Threats
Malware and Phishing Attacks
Malware and phishing attacks have become increasingly prevalent in the digital landscape, posing significant threats to browser security. Malicious software, commonly known as malware, takes advantage of vulnerabilities present in web browsers to infiltrate users’ systems. These vulnerabilities can include flaws in the browser’s code, insecure plugins or extensions, or outdated software versions.
Once inside a user’s system, malware can wreak havoc by stealing sensitive personal information, logging keystrokes, or even granting unauthorized access to cybercriminals. Phishing attacks are another form of threat that exploit human psychology rather than technical vulnerabilities.
In a phishing attack, perpetrators deceive users by creating seemingly legitimate websites or emails that mimic reputable organizations such as banks or social media platforms. Through clever tactics like spoofing URLs and crafting persuasive messages, attackers trick unsuspecting individuals into revealing their confidential information such as login credentials or financial details.
Cross-Site Scripting (XSS) Attacks
Cross-Site Scripting (XSS) attacks are a common technique employed by hackers to inject malicious scripts into webpages viewed by users. This vulnerability occurs when a website fails to properly validate user-supplied input before displaying it on its pages.
By exploiting this weakness, attackers can insert harmful code that executes within the victim’s browser context. The consequences of an XSS attack can be severe and wide-ranging.
From stealing session cookies and hijacking user accounts to defacing websites and spreading malware to visitors—XSS exposes both users and website owners to considerable risks. Notably, several high-profile cases have demonstrated the potential impact of XSS attacks; for instance, attackers compromising popular social media platforms’ security through cross-site scripting have caused widespread chaos.
Man-in-the-Middle (MitM) Attacks
In the intricate realm of cybersecurity, Man-in-the-Middle (MitM) attacks pose a significant threat to the privacy and confidentiality of online communications. These attacks occur when an attacker intercepts the communication between a user and a website, serving as an unauthorized intermediary unbeknownst to both parties involved. The mechanics of MitM attacks involve the attacker intercepting data exchanged between the user’s browser and the website by exploiting vulnerabilities in public Wi-Fi networks or compromised network routers.
By gaining access to this intermediary position, attackers can eavesdrop on sensitive information such as login credentials, credit card details, or personal conversations. To counteract MitM attacks, robust encryption protocols such as Secure Socket Layer (SSL) or Transport Layer Security (TLS) are crucial.
By encrypting data transmitted between users and websites, SSL/TLS protocols ensure that intercepted information remains indecipherable to malicious actors. Implementing these encryption mechanisms significantly reduces the risk of falling victim to Man-in-the-Middle attacks while reinforcing browser security. To protect your digital sanctuary from these pervasive threats, it is essential to understand their inner workings and adopt proactive security measures.
Browser Security Features and Best Practices
Secure Socket Layer/Transport Layer Security (SSL/TLS) protocols
Fortifying the Digital Fortress: The Shield of SSL/TLS One of the fundamental pillars of browser security is the implementation of Secure Socket Layer/Transport Layer Security (SSL/TLS) protocols. These encryption protocols provide a robust mechanism to secure online communication, ensuring data confidentiality, integrity, and authenticity.
When you visit a website secured with SSL/TLS, your browser establishes a secure connection by encrypting the data exchange between your device and the web server. This encryption process involves cryptographic algorithms that scramble your sensitive information into an indecipherable code, safeguarding it from eavesdroppers and potential attackers.
Content Security Policy (CSP)
Warding off Malevolent Scripts: The Power of CSP Content Security Policy (CSP) acts as a guardian against one of the most prevalent threats in modern web browsing: cross-site scripting (XSS) attacks. By defining strict rules regarding which types of content can be loaded on a webpage, CSP prevents malicious scripts injected into compromised websites from executing in users’ browsers.
It achieves this by specifying allowed sources for scripts, stylesheets, fonts, images, and other resources that can be loaded by the page. For instance, implementing CSP with the directive “script-src ‘self’;” allows scripts to be executed only from the same domain as the webpage itself.
Examples showcasing implementation techniques for CSP:
– Utilizing nonce attributes to validate specific inline scripts. – Employing Content-Security-Policy headers in HTTP responses. – Leveraging the ‘report-uri’ directive to receive violation reports.
Same-Origin Policy (SOP)
Unbreakable Boundaries: SOP Shielding against XSS The Same-Origin Policy (SOP) is a vital defense mechanism in browsers to mitigate cross-site scripting (XSS) attacks, which exploit the trust between different websites.
SOP restricts web pages from accessing or manipulating content from other origins, unless specifically permitted. Essentially, this policy ensures that scripts running in one domain cannot tamper with or read data from another domain.
While SOP forms a robust security boundary, it’s crucial to understand its exceptions and potential risks. Some exceptions include cross-origin resource sharing (CORS) and the use of iframe elements for embedding third-party content.
Discussion on exceptions to SOP and potential risks:
– Cross-Origin Resource Sharing (CORS) and its impact on SOP. – The risks of allowing unrestricted cross-origin communication. – Potential bypass techniques used by attackers to exploit weak points in SOP.
Automatic Updates
Staying Ahead of the Curve: The Importance of Automatic Updates Browser developers fully understand the ever-evolving nature of security threats lurking on the internet. That’s why automatic updates play a critical role in maintaining browser security.
By regularly releasing patches, bug fixes, and feature updates, browser vendors ensure that users benefit from enhanced protection against emerging vulnerabilities and attacks. Keeping your browser up-to-date not only improves its performance but also ensures that you have access to the latest security features implemented by developers.
Conclusion
In an ever-connected digital world fraught with evolving threats, safeguarding our browsing experience becomes an imperative task. The realm of browser security encompasses a multifaceted approach, combining the robust encryption provided by SSL/TLS protocols, the vigilant protection offered by Content Security Policy (CSP), the strong boundaries set by Same-Origin Policy (SOP), and the constant fortification through automatic updates. By adhering to best practices and staying proactive in embracing these security measures, we can confidently navigate cyberspace with reduced risks.
While it is easy to become disheartened by the ceaseless cat-and-mouse game between hackers and cybersecurity defenders, understanding and implementing these browser security features instills a sense of hope and optimism. With ever-advancing technology and collective efforts from web developers, we can effectively fortify our digital experiences, ensuring a safer online future for all.